摘要
前置条件:安装 AWS Load Balancer Controller 附加组件
Service
service与elb的绑定关系是通过注释实现的。这里service必须设置为LoadBalancer,一个service就对应一个elb。
创建服务后,请勿编辑注释。如果需要对其进行修改,请删除相应服务对象,然后使用此注释的所需值重新创建它。
service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing 表示允许外网访问,如果只允许集群内部访问,则去掉该注释即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 --- apiVersion: v1 kind: Namespace metadata: name: nlb-sample-app --- apiVersion: apps/v1 kind: Deployment metadata: name: nlb-sample-app namespace: nlb-sample-app spec: replicas: 3 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: public.ecr.aws/nginx/nginx:1.21 ports: - name: tcp containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nlb-sample-service namespace: nlb-sample-app annotations: service.beta.kubernetes.io/aws-load-balancer-type: external service.beta.kubernetes.io/aws-load-balancer-nlb-target-type: ip service.beta.kubernetes.io/aws-load-balancer-scheme: internet-facing spec: ports: - port: 80 targetPort: 80 protocol: TCP type: LoadBalancer selector: app: nginx
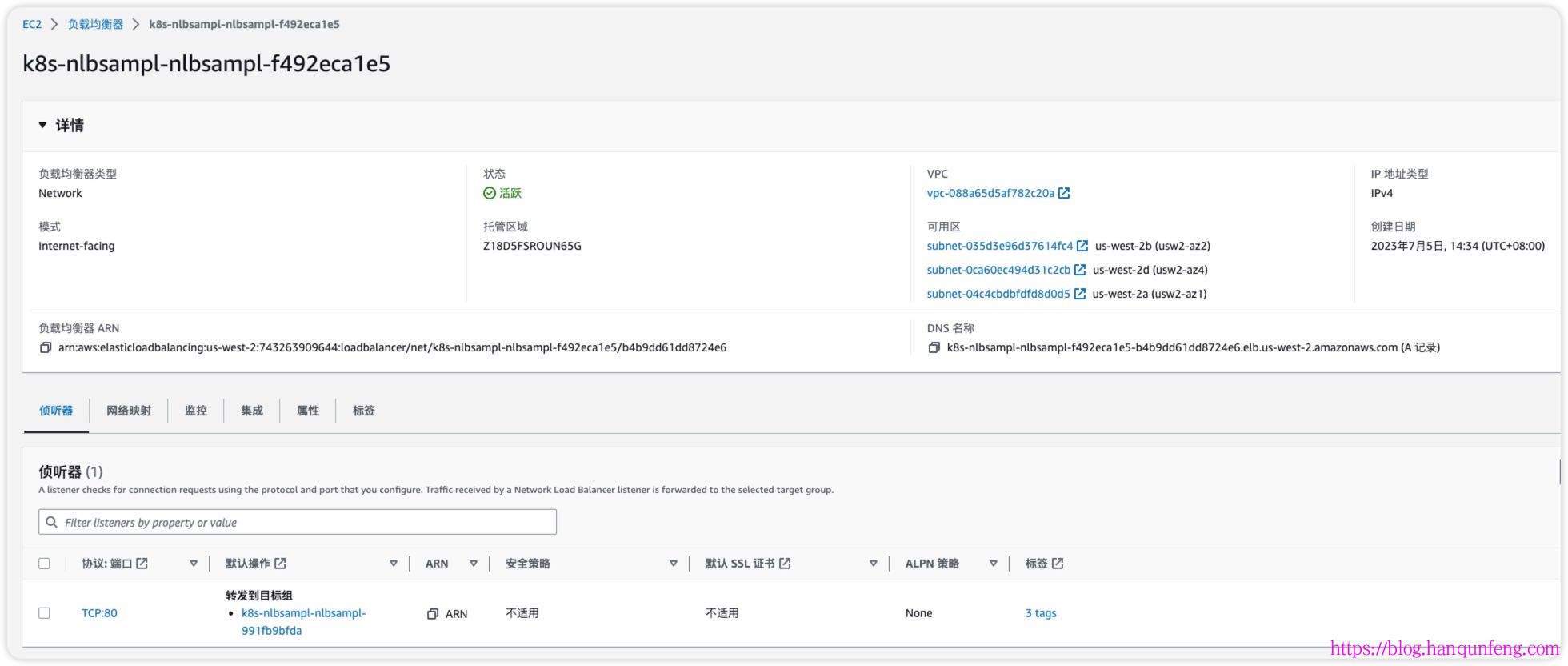
1 2 3 4 $ k apply -f eks-loadbalancer-service.yaml $ k get svc -n nlb-sample-app NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE nlb-sample-service LoadBalancer 10.100.176.186 k8s-nlbsampl-nlbsampl-f492eca1e5-b4b9dd61dd8724e6.elb.us-west-2.amazonaws.com 80:31743/TCP 6m11s
Ingress
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 apiVersion: v1 kind: Namespace metadata: name: game-2048 --- apiVersion: apps/v1 kind: Deployment metadata: namespace: game-2048 name: deployment-2048 spec: selector: matchLabels: app.kubernetes.io/name: app-2048 replicas: 5 template: metadata: labels: app.kubernetes.io/name: app-2048 spec: containers: - image: public.ecr.aws/l6m2t8p7/docker-2048:latest imagePullPolicy: Always name: app-2048 ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: namespace: game-2048 name: service-2048 spec: ports: - port: 80 targetPort: 80 protocol: TCP type: ClusterIP selector: app.kubernetes.io/name: app-2048
1 $ k apply -f service.yaml
测试用的ingress.yaml
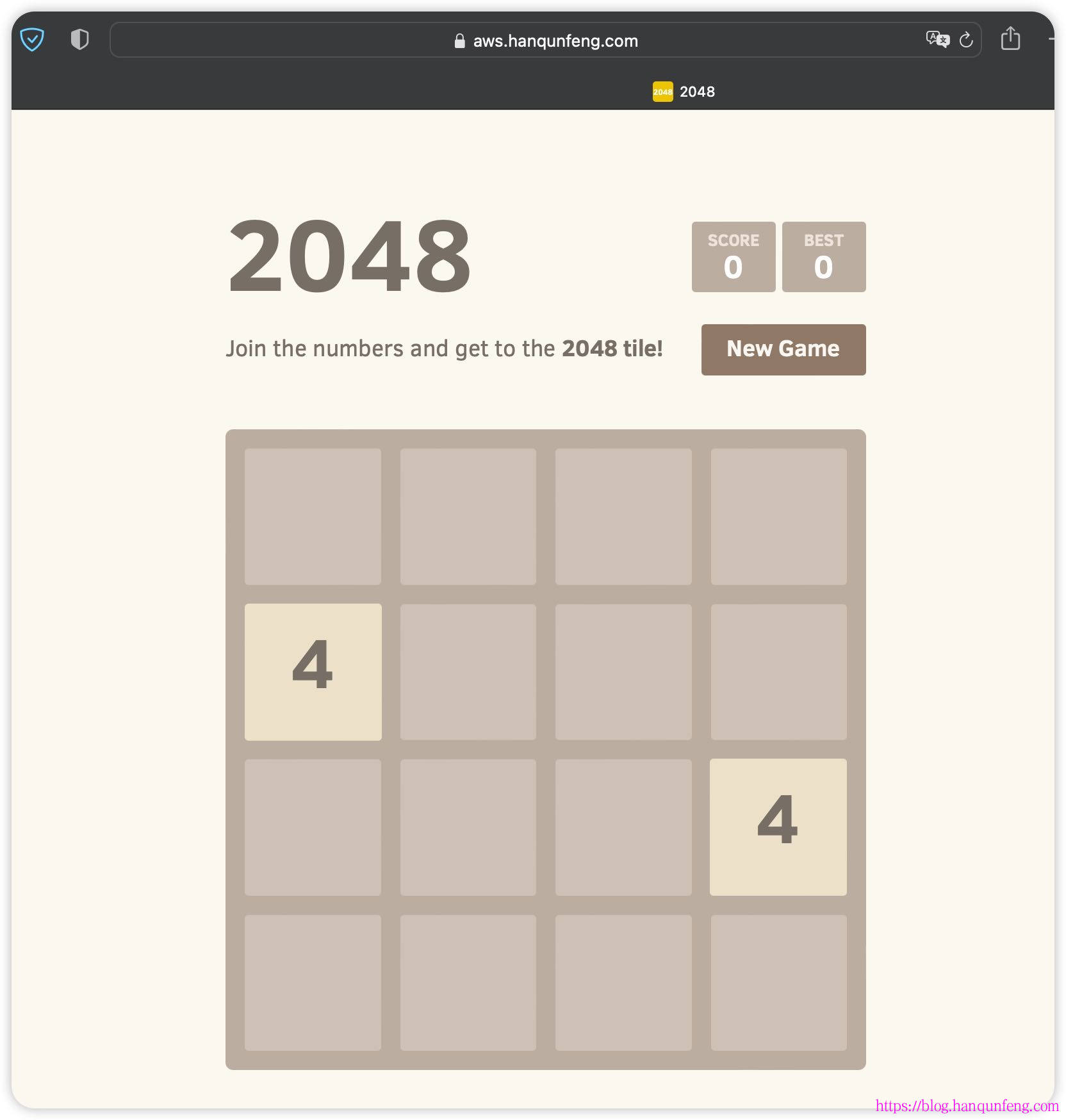
这里为了演示,host都指向了同一个service
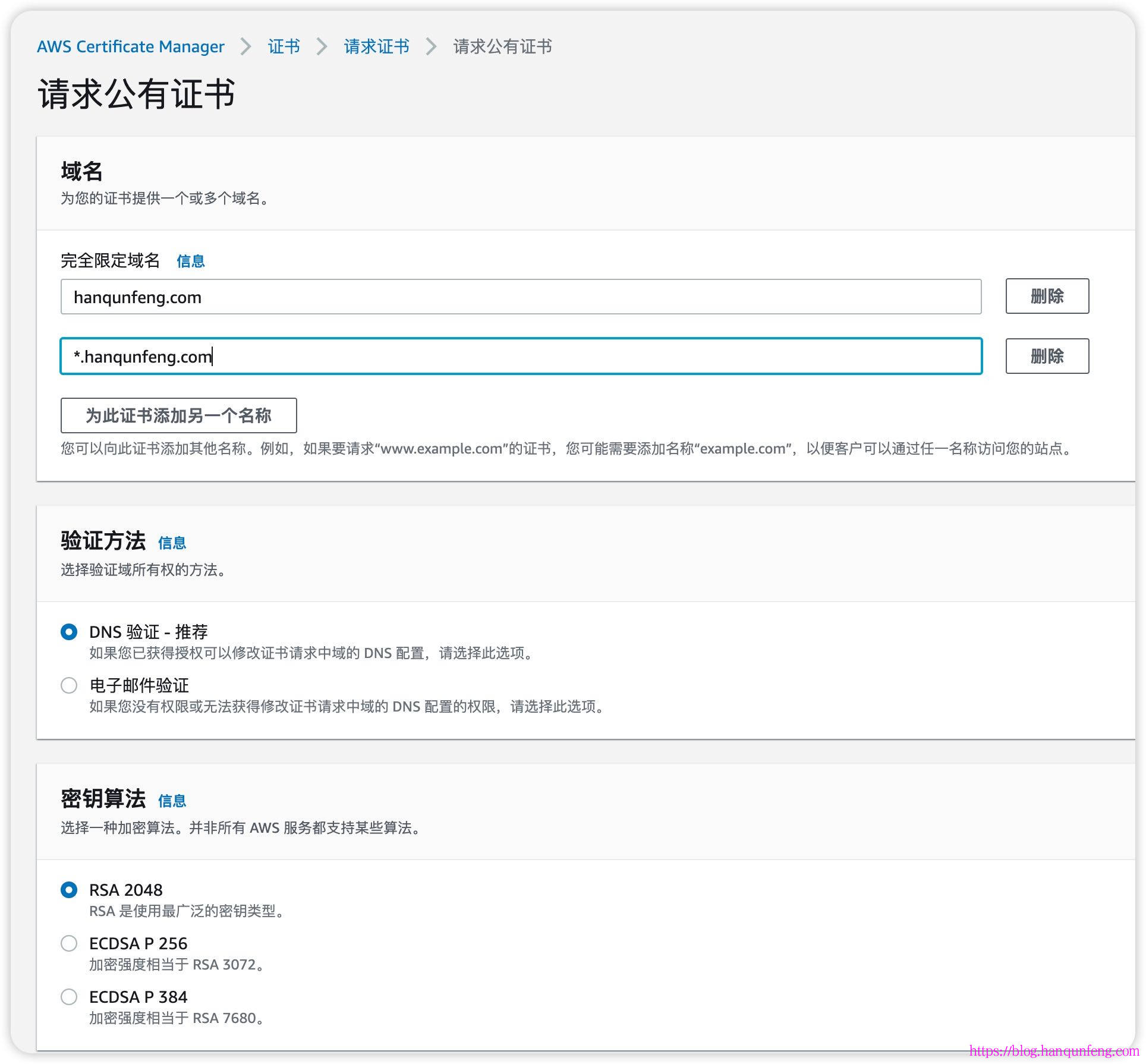
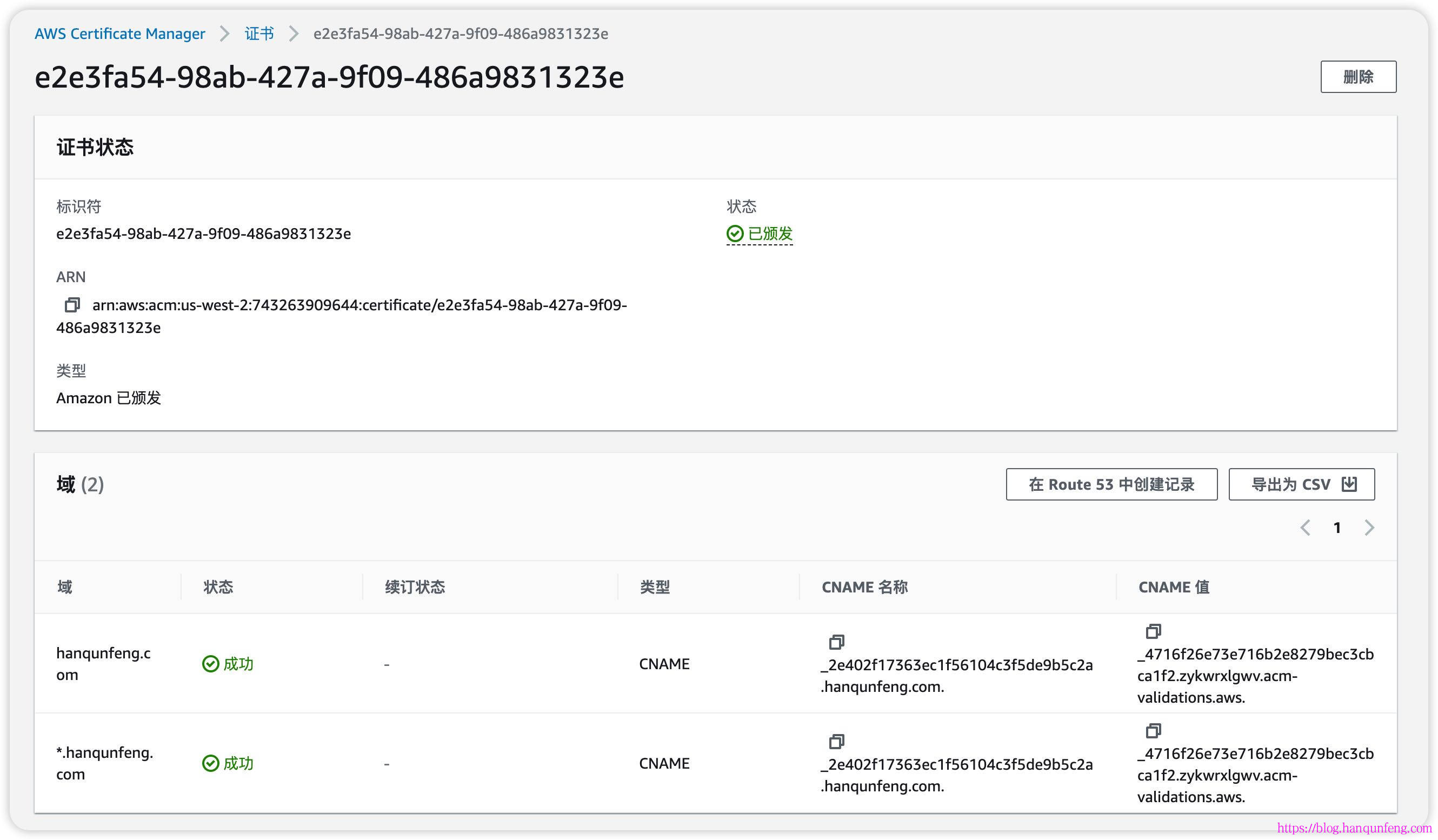
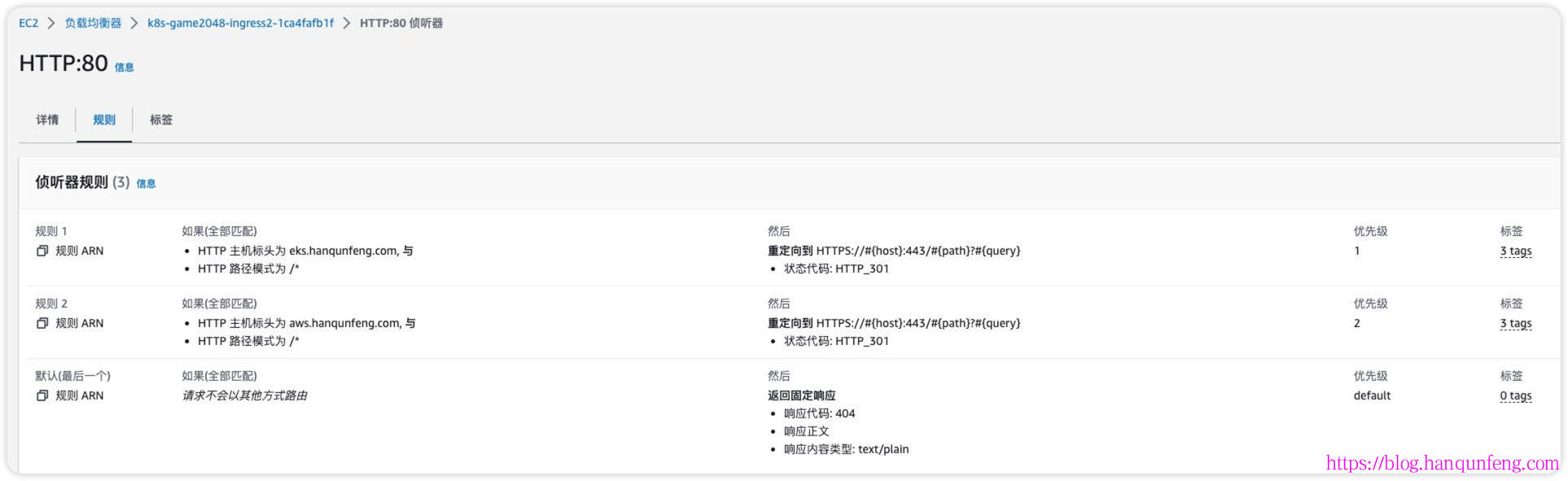
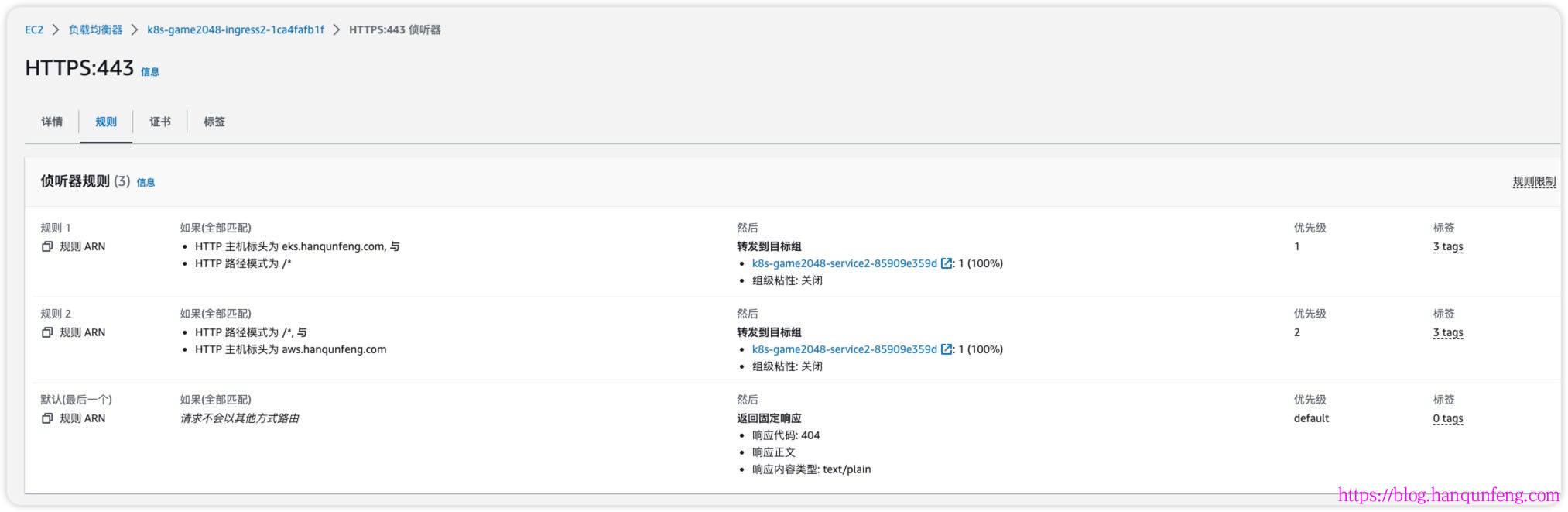
ingress是通过注释实现与elb的绑定,包括监听端口、80重定向到443、https证书等等
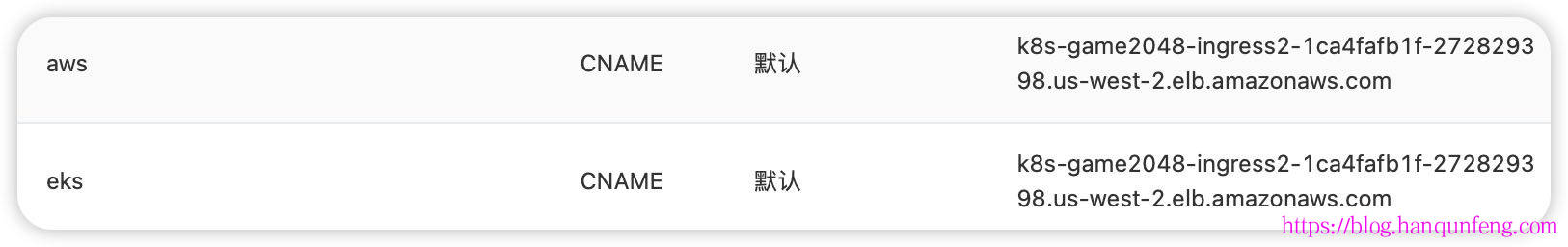
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 apiVersion: networking.k8s.io/v1 kind: Ingress metadata: namespace: game-2048 name: ingress-2048 annotations: alb.ingress.kubernetes.io/actions.ssl-redirect: '{"Type": "redirect", "RedirectConfig":{ "Protocol": "HTTPS", "Port": "443", "StatusCode": "HTTP_301"}}' alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:us-west-2:743263909655:certificate/e2e3fa54-98ab-427a-9f09-486a9831323e alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS":443}]' alb.ingress.kubernetes.io/scheme: internet-facing alb.ingress.kubernetes.io/target-type: ip spec: ingressClassName: alb rules: - host: eks.hanqunfeng.com http: paths: - path: / pathType: Prefix backend: service: name: ssl-redirect port: name: use-annotation - path: / pathType: Prefix backend: service: name: service-2048 port: number: 80 - host: aws.hanqunfeng.com http: paths: - path: /* pathType: ImplementationSpecific backend: service: name: ssl-redirect port: name: use-annotation - path: /* pathType: ImplementationSpecific backend: service: name: service-2048 port: number: 80
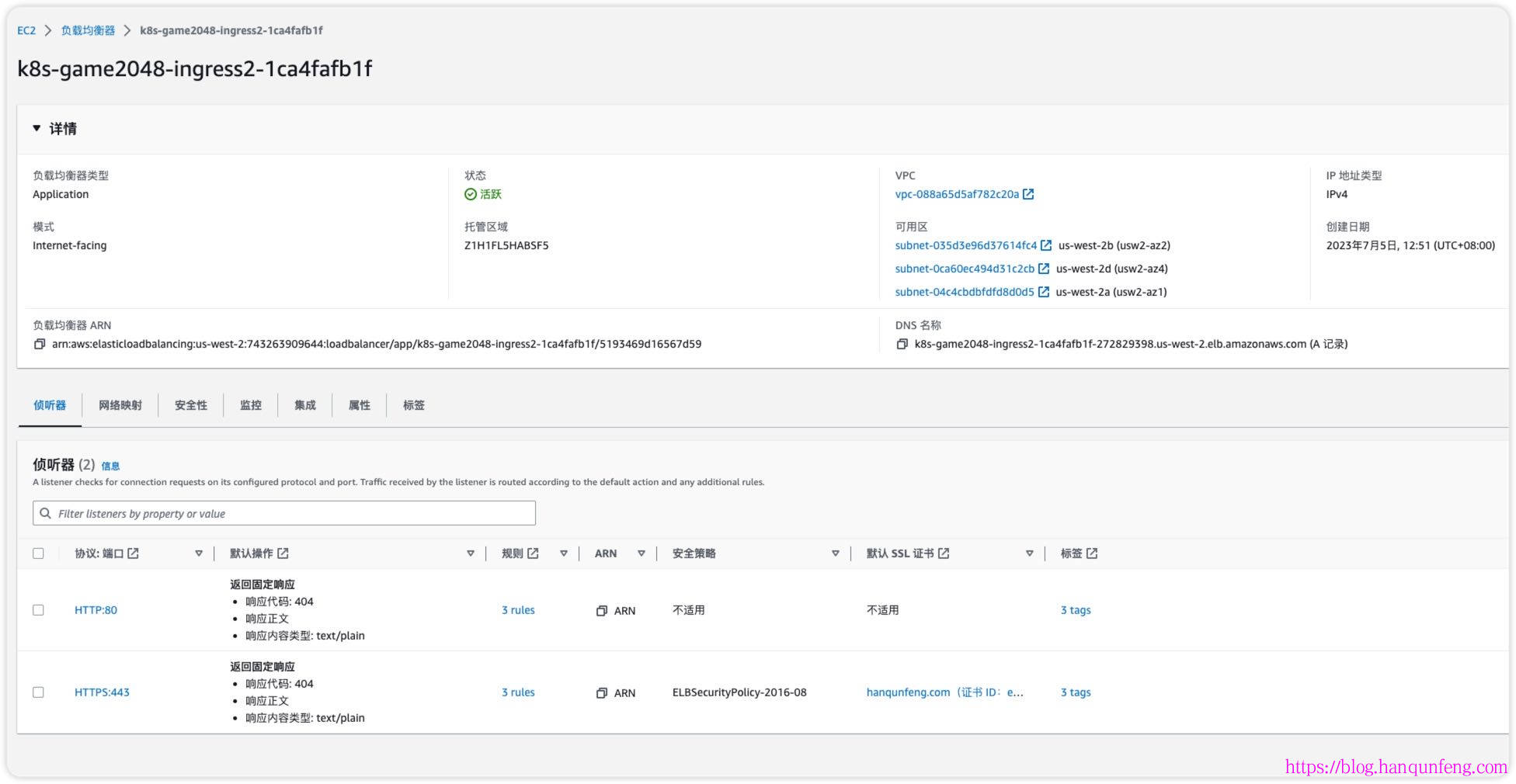
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 $ k apply -f ingress.yaml $ k describe ing -n game-2048 ingress-2048 Name: ingress-2048 Labels: <none> Namespace: game-2048 Address: k8s-game2048-ingress2-1ca4fafb1f-272829398.us-west-2.elb.amazonaws.com Ingress Class: alb Default backend: <default> Rules: Host Path Backends ---- ---- -------- eks.hanqunfeng.com / ssl-redirect:use-annotation (<error: endpoints "ssl-redirect" not found>) / service-2048:80 (192.168.0.196:80,192.168.20.125:80,192.168.22.188:80 + 2 more...) aws.hanqunfeng.com /* ssl-redirect:use-annotation (<error: endpoints "ssl-redirect" not found>) /* service-2048:80 (192.168.0.196:80,192.168.20.125:80,192.168.22.188:80 + 2 more...) Annotations: alb.ingress.kubernetes.io/actions.ssl-redirect: {"Type" : "redirect" , "RedirectConfig" :{ "Protocol" : "HTTPS" , "Port" : "443" , "StatusCode" : "HTTP_301" }} alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:us-west-2:743263909655:certificate/e2e3fa54-98ab-427a-9f09-486a9831323e alb.ingress.kubernetes.io/listen-ports: [{"HTTP" : 80}, {"HTTPS" :443}] alb.ingress.kubernetes.io/scheme: internet-facing alb.ingress.kubernetes.io/target-type: ip Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal SuccessfullyReconciled 2s ingress Successfully reconciled
在 Kubernetes Ingress 规则中,pathType 有三种可能的取值
Exact: 使用 Exact 类型时,请求的路径必须与规则中指定的路径完全匹配,包括大小写。这是最精确的匹配方式。
Prefix: 使用 Prefix 类型时,请求的路径只需以规则中指定的路径为前缀即可匹配。这种方式可以处理以指定路径为前缀的所有请求。
ImplementationSpecific: 使用 ImplementationSpecific 类型时,路径匹配的行为由 Ingress 控制器的具体实现决定。这种类型的路径匹配方式在不同的 Ingress 控制器中可能会有所差异,因此具体行为可能会因实现而异。在 AWS ALB Ingress Controller 中,pathType 的 ImplementationSpecific 类型可以与多个 AWS Load Balancer 的功能集成,包括 Application Load Balancer (ALB)、Network Load Balancer (NLB) 和 Classic Load Balancer (CLB)。我们这里使用的是ALB。