AWS-EKS-18--Autoscaling 之 Cluster Autoscaler(CAS)
摘要
-
本文介绍EKS集群Autoscaling 之 Cluster Autoscaler(CAS)
-
参考资料:
EKS集群Autoscaling
-
弹性伸缩是一项功能,可以自动上下伸缩您的资源以满足不断变化的需求。
-
Amazon EKS 支持两款自动扩缩产品:
- Cluster Autoscaler(CAS) ,本文就介绍这款产品的使用方法。
- Karpenter,参看 AWS-EKS-19--Autoscaling 之 Karpenter
Cluster Autoscaler(CAS)是什么?
-
Cluster Autoscaler是一个可以自动调整Kubernetes集群大小的组件,以便所有pod都有运行的地方,并且没有不需要的节点。支持多个公共云提供商。 -
AWS EKS集群自动扩容功能可以基于Cluster Autoscaler自动调整集群中node的数量以适应需求变化。 -
Cluster Autoscaler一般以Deployment的方式部署在K8s中,通过service account赋予的权限来访问AWS autoscaling group资源,并控制node(EC2)的增减。 -
AWS EKS Cluster Autoscaler以Amazon EC2 Auto Scaling Groups服务为基础对node进行扩容,所以其扩容或缩容时,也要遵守节点组扩缩中的配置

-
当有新的Pod无法在现有node上schedule时会触发扩容,当node空闲超过10min时,会触发缩容。
-
Cluster Autoscaler的镜像版本要求与K8s版本匹配,所以当EKS(K8s)升级时,Cluster Autoscaler的镜像也要进行升级。
创建IAM策略和角色
-
创建Policy:
cluster-autoscaler-policy.json
1 | { |
1 | $ export AWS_PROFILE=eks-ty-old |
-
创建IAM Role的信任关系:
trust-policy.json
1 | { |
-
创建 IAM Role
1 | $ aws iam create-role \ |
-
为 Role 添加 Policy
1 | $ aws iam attach-role-policy \ |
部署Cluster Autoscaler
-
下载Autoscaler yaml文件
1 | #下载yaml文件,github仓库中的文件下载路径格式为:https://raw.githubusercontent.com/<Owner>/<RepositoryName>/<branch>/<FilePath> |
-
修改yaml文件配置
打开Cluster Autoscaler的github地址,查看与EKS版本匹配的最新Autoscaler镜像版本

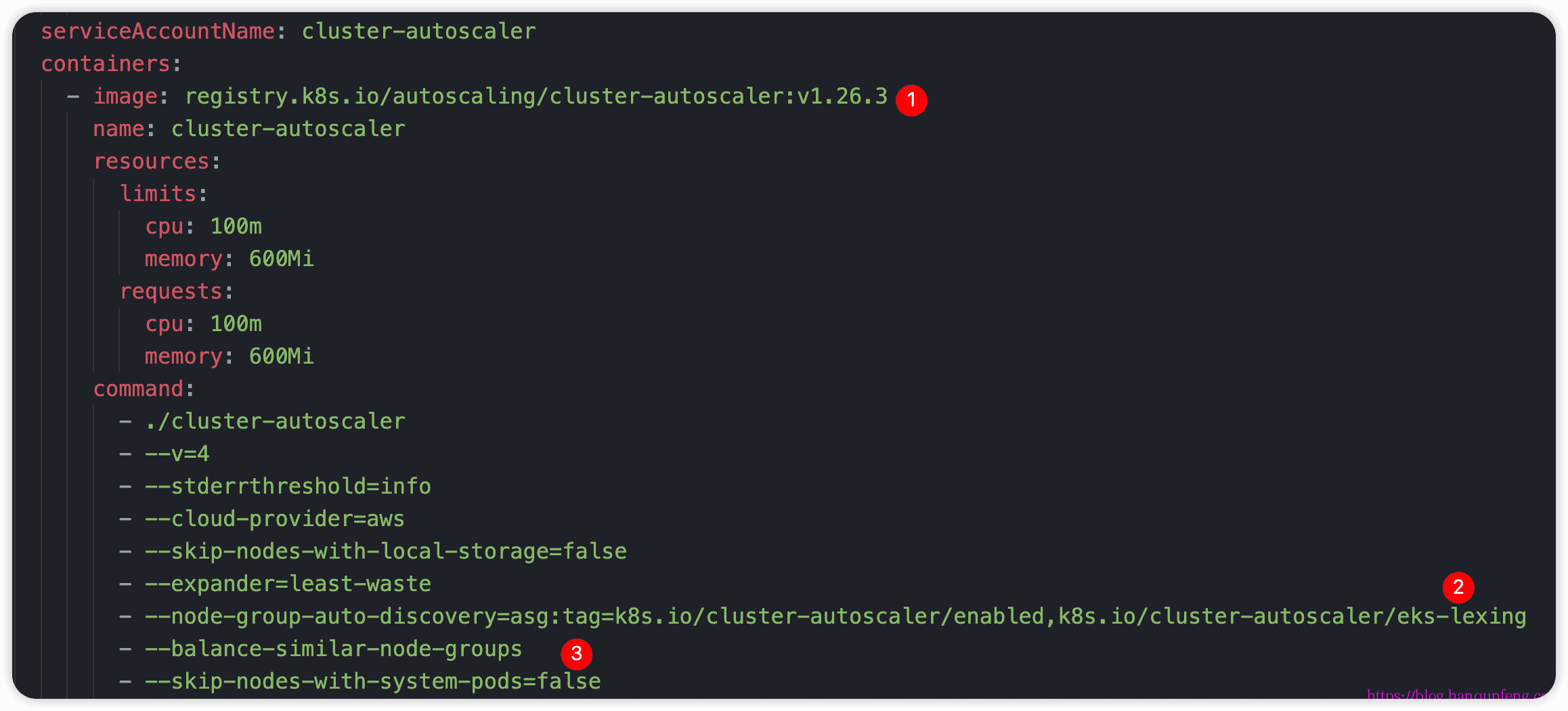
- 1.把cluster-autoscaler的镜像版本换成上面查到的版本1.26.3
- 2.查找并替换“
”为我们EKS的名称: eks-lexing - 3.在EKS的名称“tsEKS”下面,并添加以下两行
1
2- --balance-similar-node-groups
- --skip-nodes-with-system-pods=false--balance-similar-node-groups:此选项用于启用集群节点组的负载均衡功能。当你有多个具有相似容量的节点组时,启用此选项可以确保 Cluster Autoscaler 尽可能均衡地在这些节点组之间分配 Pod。它帮助确保节点组的资源利用率更加平衡,以提高集群的整体性能。
--skip-nodes-with-system-pods=false:此选项用于设置是否跳过具有系统 Pod 的节点。默认情况下,Cluster Autoscaler 会跳过具有系统 Pod(如 kube-system 命名空间中的核心组件)的节点,以确保这些关键组件的正常运行。将该选项设置为 false,即禁用跳过具有系统 Pod 的节点,可以让 Cluster Autoscaler 考虑包括具有系统 Pod 的节点在内的所有节点进行调整。- 4.为ServiceAccount添加IMA Role注解,注意一定要添加这个注解后再进行部署,否则会提示没有权限

-
部署Cluster Autoscaler
1 | $ kubectl apply -f cluster-autoscaler-autodiscover.yaml |
-
查看Cluster Autoscaler Deployment
1 | # cluster-autoscaler |
-
给autoscaler deployment打patch,增加annotation
1 | # 这个注解的作用是告诉 Kubernetes 系统不要将这些 Pod 标记为可以被安全驱逐(evict)的 Pod。 |
测试
-
查看当前node节点
1 | $ k get node |
-
创建测试用的deployment:
testDeploy.yaml
1 | apiVersion: apps/v1 |
1 | $ k apply -f testDeploy.yaml |
-
过一会查看node情况
1 | # 可以看到新创建了一个node节点 |
-
缩容deploy
1 | # 将副本降为1 |
-
大约过10几分钟就可以看到新增的node已经下线
1 | $ k get node |
升级Cluster Autoscaler
-
Cluster Autoscaler的镜像版本要求与K8s版本匹配,所以当EKS(K8s)升级时,Cluster Autoscaler的镜像也要进行升级。
1 | $ kubectl set image deployment cluster-autoscaler \ |
关闭Cluster Autoscaler
1 | $ k scale deploy cluster-autoscaler -n kube-system --replicas 0 |
